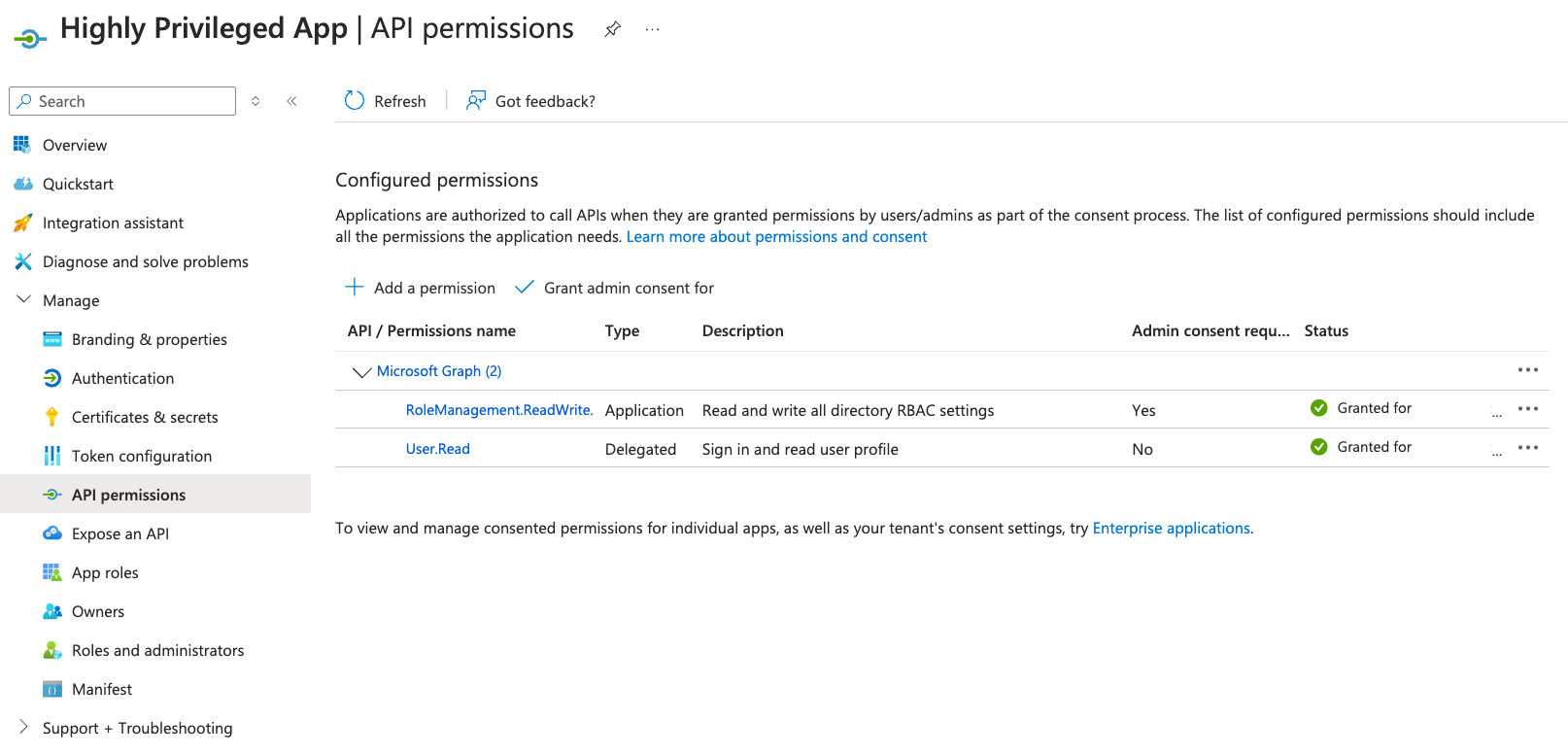
I recently wrote a blog for BeyondTrust, explaining some known Entra ID app escalations. I documented the exact attack paths threat actors can use, as well as defenses to prevent attacks.
To see the full article head over to BeyondTrust’s blog:
https://www.beyondtrust.com/blog/entry/entra-id-app-escalations.
Enjoy the read!